 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
4. Captcha Security
2024-01-22
Questions
Question 1: How to use Captcha correctly?
Question 2: How to use SMS Verification Code correctly?
Question 2: How to use Email Verification Code correctly?
Units
1. A Simple Captcha
2. Error 1: verification code is empty
3. Error 2: verification code is too simple
4. Error 3: check verification code at client side only
5. Error 4: save verification code to cookie
6. Error 5: not destroy verification code in time
7. Error 6: captcha file name expose the verification code
8. Error 7: not bind verification code to business logic
1. A Simple Captcha
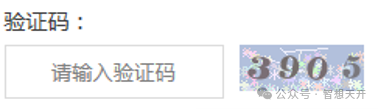
The following is a simple captcha:
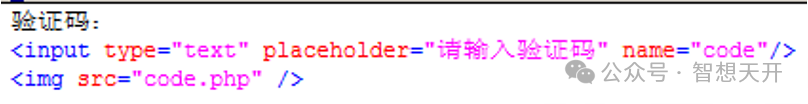
The following is the HTML code of the captcha:
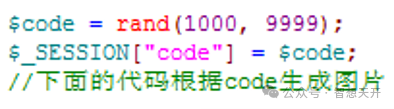
The following is a simple PHP code to generate verification code:
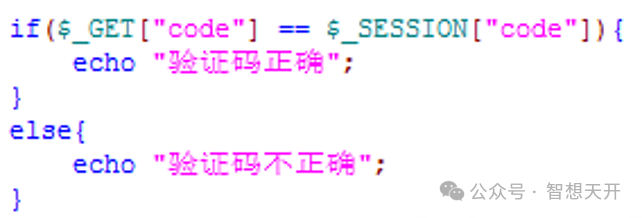
The following is a simple PHP code to verify the code:
2. Error 1: verification code is empty
The verification code is generated and stored into session when the image is requested. So if user don't request for the image, the session will keep empty. Thus, when we request the server with an empty code, the PHP check, such as $_GET[“code”] == $_SESSION[“code”], is valid. So we skip the verification code check successfully.
To resolve this problem, we must check whether $_SESSION[“code”] is empty.
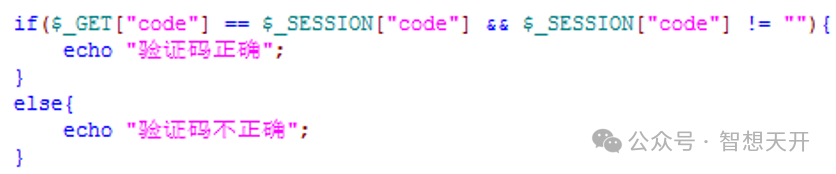
3. Error 2: verification code is too simple
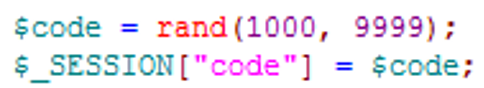
Four digital code is too simple for important conditions, such as find password. The attack can be made by request the server repeatedly.
To resolve this problem, we should keep the verification code long and complex enough. If use MD5, we should ensure the origin string to be with alphanumeric and special symbols, and the length should be longger than 10.
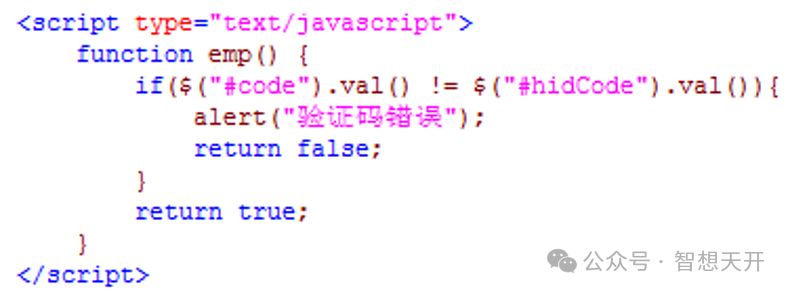
4. 3: check verification code at client side only
Use JavaScript to check verification code at client side only, may be easily bypassed using Form Submission Deception Attack. So all check should be performed at server side.
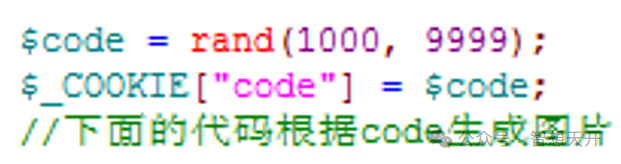
5. Error 4: save verification code to cookie
Some verification code, such as email verification code, we need to save it for later use. The following code which saved the verification code to cookie is incorrect, for the attacker may read the cookie easily, this makes the verification code exposed.
To resolve this problem, we must only save the verification code at server side instead of cookie. We can save it into database, redis or so on.
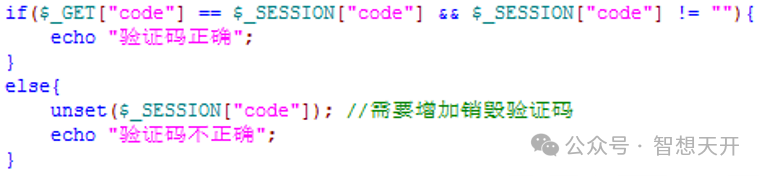
6. Error 5: not destroy verification code in time
Such code as following, when the verify failed, the verification code is not destroyed. So the attacker can try the correct code by repeatly request the server. For 4 digit code, it will be very quick for the attacker to try.
To resolve this problem, we must destroy the verification code in time. The next time user request the verification code, it's regenerated. This will add difficulty for repeatly attacks.
7. Error 6: captcha file name expose the verification code
For example, if use the captcha as following, the user can find the actual code easily by view the page source.

To resolve this problem, we should use file names without meaning, such as code.php.
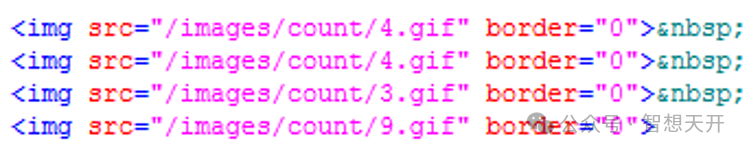
8. Error 7: not bind verification code to business logic
For example, at find password's process, user can change password after verify the verification code. Using the following code, attacker can pass any userId to the server to change any user's password.
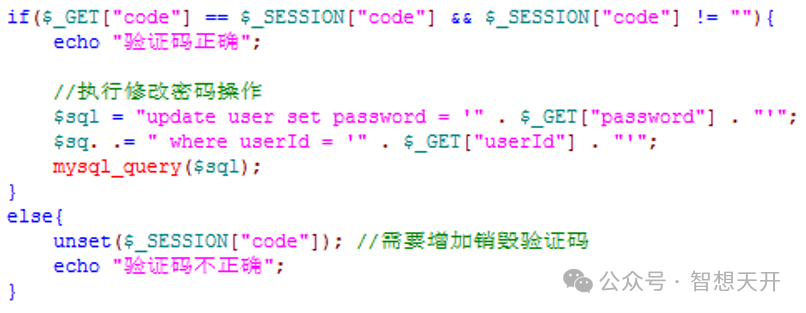
To resolve this problem, for important operations, such as change password, the important parameters, such as userId, should bind to verification code and cannot be arbitratied passed by the user. The method of bind can use database or session, but cannot be cookie.
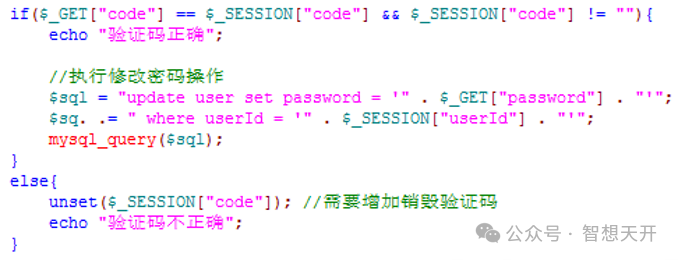

Follow us at WeChat to get more info