 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
10. Enhancing Database Security
2024-06-30
Questions
Question 1. What is database security?
Question 2. Why is database security important? What are the main threats to it?
Question 3. How can database security be enhanced?
Units
1. What is database security?
2. Examples of database security threats
3. How to enhance database security
1. What is Database Security?
Database security refers to the collective measures used to protect and secure a database management system from illicit use and malicious cyber threats and attacks. It involves safeguarding the data, the database management system (DBMS), and any associated applications from unauthorized access, misuse, and damage.
Background Knowledge
Database Management System (DBMS): A DBMS is software that uses a standard method to store and organize data, which can be retrieved and manipulated efficiently. Examples include MySQL, PostgreSQL, Oracle, etc.
Permissions and Access Control: Databases use permissions and access control to manage who can access and modify the data. This involves setting user roles and permissions to restrict unauthorized actions.
2. Examples of Database Security Threats
Database security faces various threats, including but not limited to:
1. SQL Injection
Attackers exploit vulnerabilities in an application's software to inject malicious SQL code, gaining unauthorized access to the database.
Attack Example Code
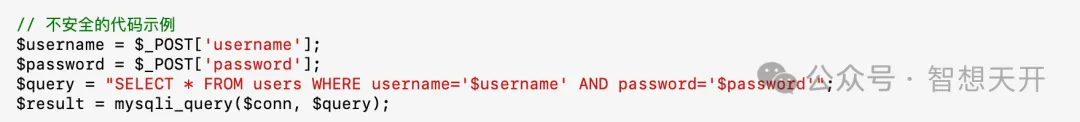
2. Privilege Escalation
Attackers exploit vulnerabilities to elevate their privileges, gaining access to sensitive data and database functions.
Attack Example Code

3. Data Breach
Sensitive data is accessed or stolen during transmission or from the database itself.
Attack Example Code

3. How to Enhance Database Security
To enhance database security, the following measures can be implemented:
1. Prevent SQL Injection
Use parameterized queries or prepared statements to prevent SQL injection attacks.
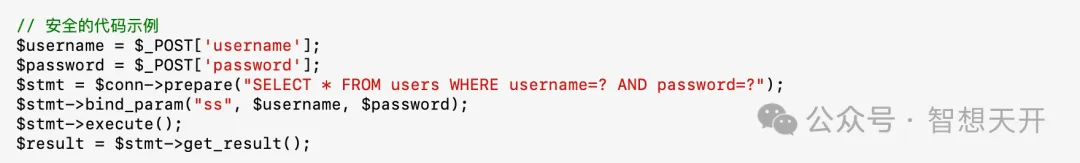
2. Manage Permissions
Set strict user permissions to ensure each user only has access to the data necessary for their role.

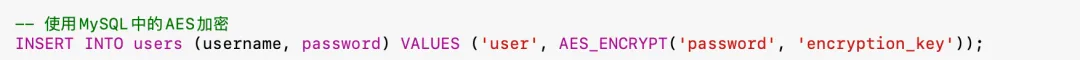
3. Encrypt Data
Encrypt sensitive data both at rest and in transit to ensure it cannot be read if intercepted or accessed unlawfully.

4. Monitoring and Logging
Enable audit logs to record all database access and actions to detect and respond to suspicious activities promptly.

5. Regular Backups
Regularly back up the database to ensure data can be restored in case of loss or corruption.

6. Updates and Patches
Regularly update the DBMS and associated software to patch known vulnerabilities.

Additional Information
Using Firewalls and Intrusion Detection Systems: Configure firewalls and intrusion detection systems (IDS) to prevent unauthorized access and detect potential threats.
Regular Audits: Conduct regular audits of database permissions and access logs to ensure compliance with security policies.
User Training: Train users on secure database practices to prevent social engineering attacks and inadvertent security breaches.
By implementing these measures, you can significantly enhance the security of the database, protect the integrity and privacy of data, and ensure the stable operation of the system.

Follow us at WeChat to get more info