 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
9. Enhancing File System Security
2024-06-27
Questions
Question 1. What is file system security?
Question 2. Why is file system security important? What are the main threats to it?
Question 3. How can file system security be enhanced?
Units
1. What is file system security?
2. Examples of file system security threats
3. How to enhance file system security
1. What is File System Security?
File system security refers to a set of strategies and techniques designed to protect data within a computer's file system from unauthorized access, tampering, and destruction. The file system is a core part of the operating system that manages and stores data. Ensuring its security is crucial for maintaining data integrity and privacy.
Background Knowledge
File System: A file system is a method and data structure that the operating system uses to manage files on a disk or partition. Common file systems include FAT32, NTFS, and EXT4.
Permissions and Access Control: File systems manage access to files and directories through permission settings (such as read, write, execute) and access control lists (ACLs).
2. Examples of File System Security Threats
File system security faces various threats, including but not limited to:
1. Unauthorized Access
Attackers may gain access to the file system by cracking passwords, exploiting vulnerabilities, or other means to read, modify, or delete sensitive data.
Attack Example Code
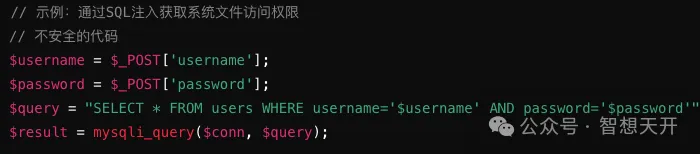
2. Data Tampering
Once attackers have access to the file system, they might alter file contents, insert malicious code, or corrupt data.
Attack Example Code
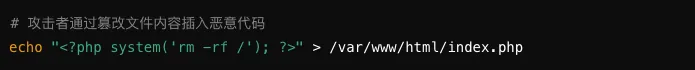
3. Data Loss or Destruction
Attackers might delete or destroy data within the file system, leading to data loss or system malfunctions.
Attack Example Code

3. How to Enhance File System Security
To enhance file system security, the following measures can be implemented:
1. Permission Management
Ensure that file and directory permissions are set appropriately, minimizing access to the necessary level to prevent unauthorized access.

2. Using Encryption
Encrypt sensitive files and data to ensure that even if data is stolen, it cannot be read.
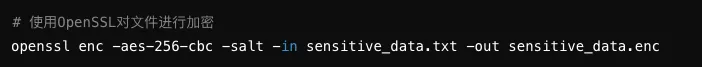
3. Regular Backups
Regularly back up the data within the file system to ensure that it can be restored in case of loss or destruction.
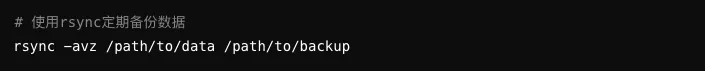
4. Monitoring and Logging
Enable file system monitoring and logging to detect and respond to abnormal activities promptly.

5. Updates and Patches
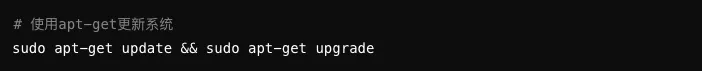
Regularly update the operating system and file system software to patch known vulnerabilities.
Additional Information
Using Firewalls and Intrusion Detection Systems: Configure firewalls and intrusion detection systems (IDS) to prevent external attackers from infiltrating the network.
Regular Audits: Regularly audit file system permissions and access logs to ensure the effectiveness of security policies.
User Training: Educate users on the secure use of the file system to prevent social engineering attacks.
By implementing these measures, you can significantly enhance the security of the file system, protect the integrity and privacy of data, and ensure the stable operation of the system.

Follow us at WeChat to get more info