 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
3. Prevention of Form Submission Deception Attacks
2024-01-15
Questions
Question 1: How Form Submission Deception Attacks arise?
Question 2: How to avoid Form Submission Deception Attacks?
Question 3: How to write security code based on the example?
Units
A simple forum
Problems on post articles
Problems on delete articles
Summarize
1. A simple forum
1.1 Table structure of the forum
1.2 A simple article list page
1.1. Table structure of the forum
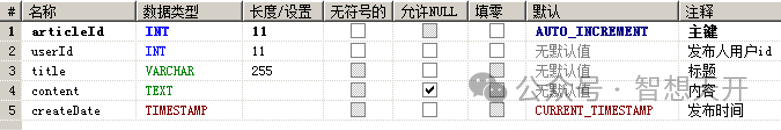
This is a sample table structure of the forum.
1.2. A simple article list page
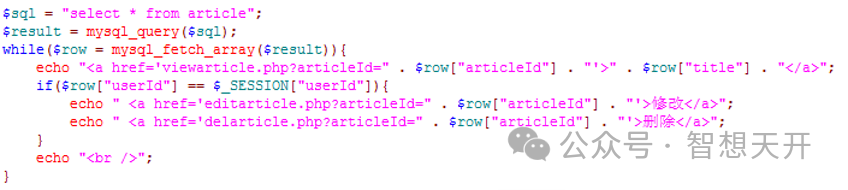
This is article list page. It allow user to modify and delete his own articles only. The current logged in user id is saved to $_SESSION[“userId”]. The modify and delete link is displayed to the owner only.
2. Problems on post articles.
2.1 A simple post code
2.2 Problems on the code
2.3 How to resolve the problems
2.1. A simple post code
The following is HTML code for post.
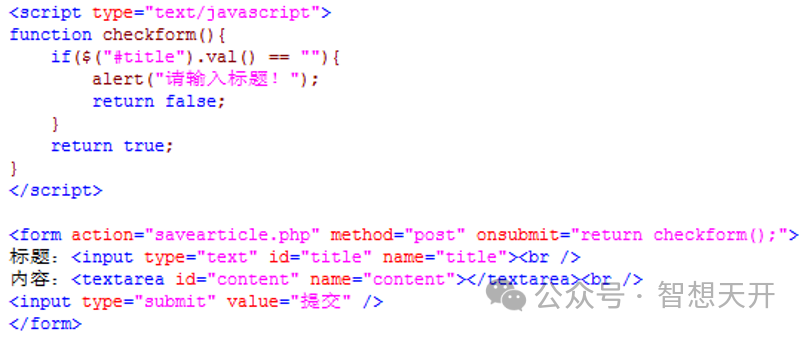
The following is the PHP handle code for post.

2.2. Problems on the code
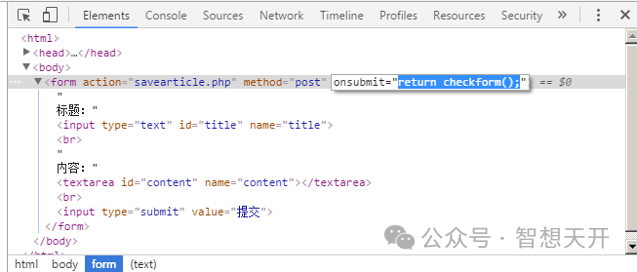
The user can easily change the client check code, to skip the verify of the JS code which don't allow the title to be empty. For example, use can use development tools provided by web browers, just delete the onsubmit method to skipped the check of JS code and post data to the server directly.
2.3 How to resolve the problems
Before save any data into database, you should check all data posted by user meets your requirement. For the previous post example, you can modify it as following:
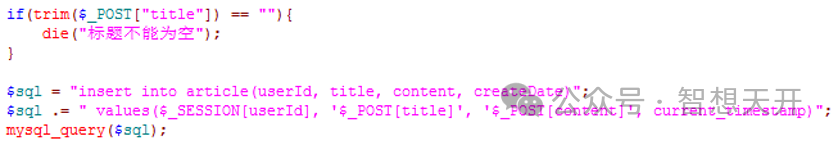
3. Problems on delete articles.
3.1 A simple delete code
3.2 Problems on the code
3.3 How to resolve the problems
3.1. A simple delete code
The following is PHP handl code for delete article.

3.2. Problems on the code
The user is not necessary to delete the article from article list's delete link only. The attacker can build delete link himself, then delete other articles. For example, The attacker can use the following PHP code to delete all the first ten thousand articles.

3.3. How to resolve the problems
1. Check the origin of the request url is legal
2. Verify the user input is valid
3.3.1. Check the origin of the request url is legal
Before perform any operation, check the origin of the request is from the same website. This may reduce some attacks to a certain degree. For the previous delete example, we can modify it as following:
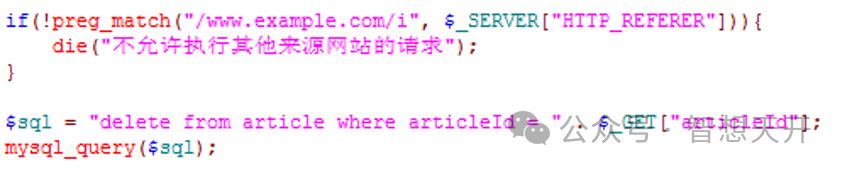
3.3.2. The disadvantages of the previous way
For the previous way, the attacker can provide a fake $_SERVER[“HTTP_REFERER”] to perform the attacker.
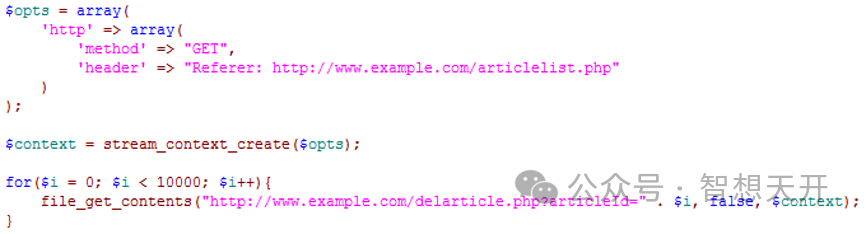
3.3.3. Verify all the user inputs are valid.
In the previous example, you should check whether the article exists before, then check the article is belonged to the operator, before actually handle the delete action. Thus, you can ensure the delete operation is safe.
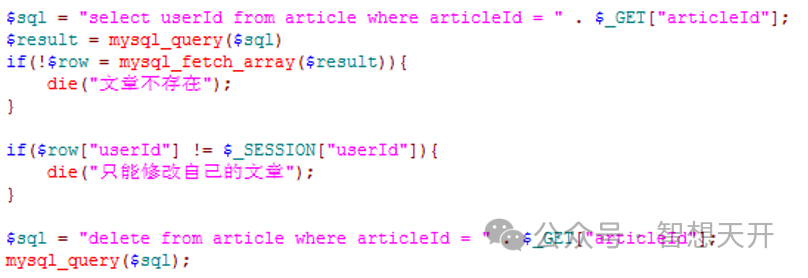
4. Summarize
Because JavaScript codes are executed on the client side, user can skip all the JavaScript codes. So you cannot rely on the client side check.
Because attacker can build fake HTTP headers, you don't know the request you received is submitted by web brower or by attacker manually. So we cannot avoid form submission deception attacks totally, we should keep this in mind.
The fundamental prevention method is to check the legality of all content input by the user. Only after all the checks passed, the subsequent real operations can be performed.

Follow us at WeChat to get more info