 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
12. Insecure Direct Object Reference
2024-07-08
Insecure Direct Object Reference (IDOR) is a common security vulnerability where an attacker can directly access unauthorized objects (such as files, database records, etc.) to obtain sensitive information or perform unauthorized operations. This article will introduce the background knowledge of IDOR, provide examples of related security issues, and discuss how to prevent these problems.
Questions
Question 1. What is Insecure Direct Object Reference (IDOR)?
Question 2. How can IDOR vulnerabilities be exploited?
Question 3. List two methods to prevent IDOR.
Units
1. Introduction to Background Knowledge
2. Example 1: User Profile Disclosure
3. Example 2: Order Information Tampering
4. Example 3: File Download Vulnerability
5. How to Prevent
6. Additional Knowledge
1. Introduction to Background Knowledge
IDOR refers to a scenario where an application uses user-provided input to access objects without sufficient access control checks. Attackers can modify these inputs to access unauthorized resources or data, leading to information leakage or data tampering. IDOR vulnerabilities exist because developers do not correctly verify whether the user has permission to access specific resources.
2. Example 1: User Profile Disclosure
Problematic Code Example:
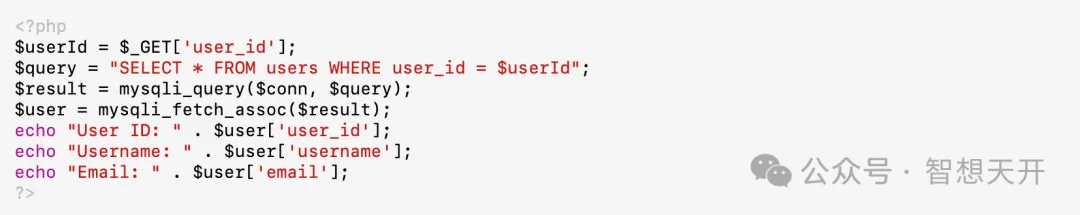
Attackers can modify the user_id parameter in the URL to access other users' profiles. For Example, the attacker can use the following url: http://example.com/profile.php?user_id=2. By modifying the user_id parameter, the attacker directly accessed and obtained the profile of the user with ID 2, leading to information leakage.
3. Example 2: Order Information Tampering
Problematic Code Example:
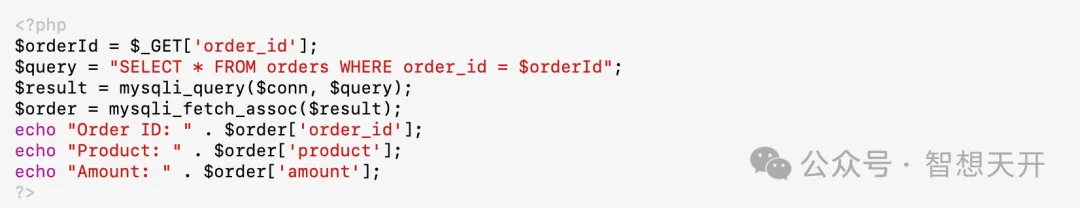
Attackers can modify the order_id parameter in the URL to view or modify other users' order information. For Example, the attacker can use the following url: http://example.com/order.php?order_id=10. By modifying the order_id parameter, the attacker directly accessed and obtained the order information with ID 10, leading to sensitive data leakage.
4. Example 3: File Download Vulnerability
Problematic Code Example:
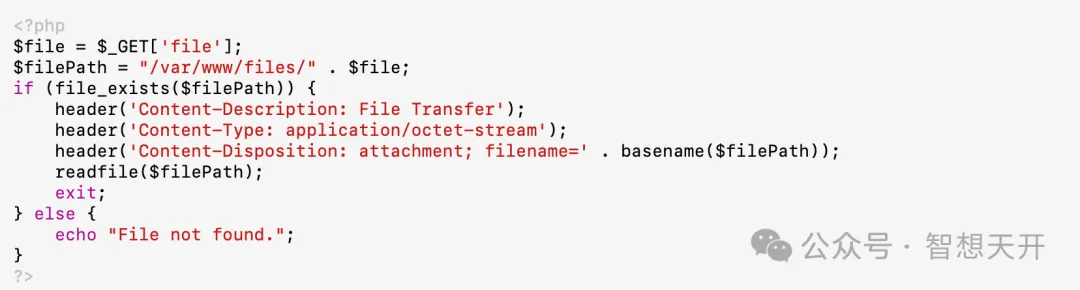
Attackers can modify the file parameter in the URL to download arbitrary files. For Example, the attacker can use the following url: http://example.com/download.php?file=../../../../etc/passwd. By modifying the file parameter, the attacker downloaded the sensitive /etc/passwd file from the server, leading to information leakage.
5. How to Prevent
5.1. Fix for Example 1: User Profile Disclosure
Fixed Secure Code:
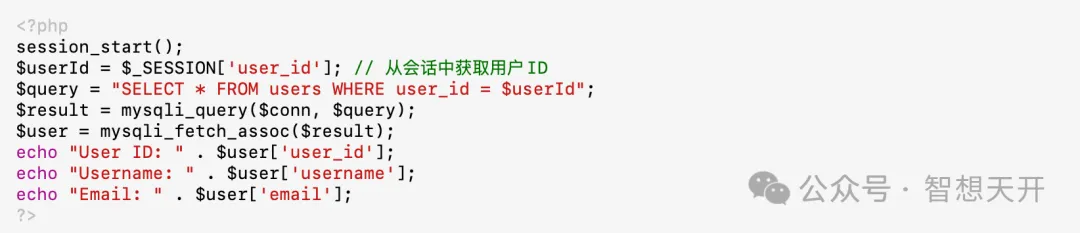
By getting the user ID from the session, the user can only access their own profile, preventing unauthorized access.
5.2. Fix for Example 2: Order Information Tampering
Fixed Secure Code:
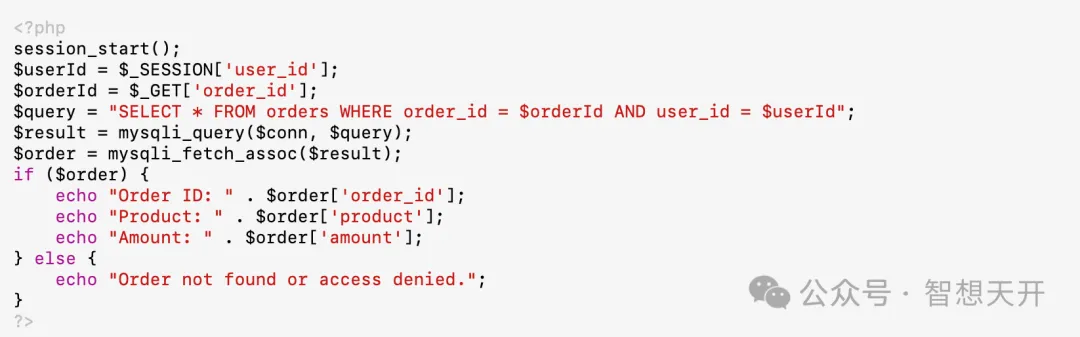
By adding a user ID check when querying order information, it ensures that users can only access their own order information, preventing data leakage and tampering.
5.3. Fix for Example 3: File Download Vulnerability
Fixed Secure Code:
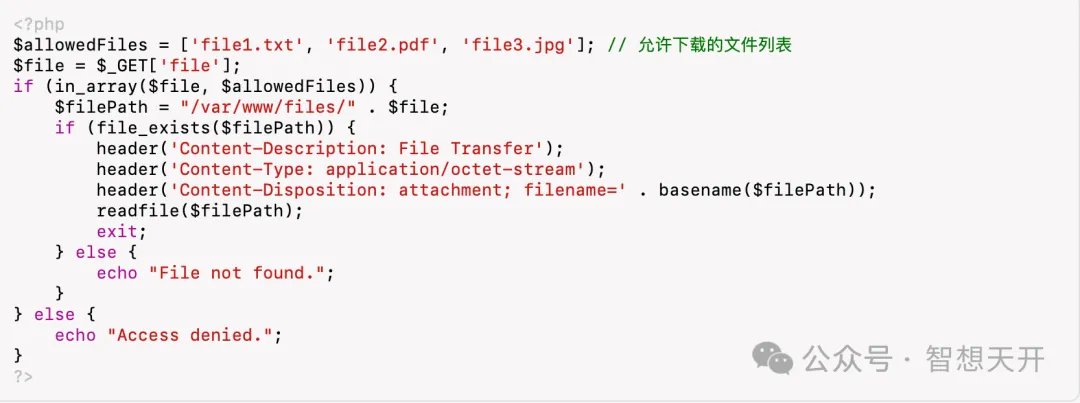
By restricting the list of allowed files for download, it prevents users from modifying parameters to download arbitrary files, ensuring the security of file downloads.
6. Additional Knowledge
Access Control Models: Learn about role-based access control (RBAC) and attribute-based access control (ABAC) models to understand how to implement fine-grained permission management.
Secure Coding Practices: Understand and follow best practices for secure coding, such as input validation, output encoding, and the principle of least privilege.
Secure Frameworks and Libraries: Use security-audited frameworks and libraries, such as OWASP's ESAPI, to help implement secure access control.
Deep Learning on Security: Read OWASP guidelines to learn more about IDOR and other security issues.

Follow us at WeChat to get more info