 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
13. Security Issues of Privilege Escalation Caused by Code
2024-07-09
Privilege escalation is when an attacker exploits vulnerabilities or errors in a program to gain higher privileges without authorization. This type of security issue can lead to attackers obtaining administrator privileges, accessing sensitive data, or performing unauthorized operations. This article will introduce the background knowledge of privilege escalation, provide some related security issue examples, and discuss how to prevent these problems.
Questions
Question 1. What is privilege escalation caused by code?
Question 2. How can attackers exploit code vulnerabilities to perform privilege escalation?
Question 3. List two methods to prevent privilege escalation.
Units
1. Introduction to Background Knowledge
2. Example 1: Unvalidated User Input
3. Example 2: Hardcoded Default Password
4. Example 3: Function Lacking Permission Check
5. How to Prevent
6. Additional Knowledge
1. Introduction to Background Knowledge
Privilege escalation refers to attackers exploiting vulnerabilities in a system or application to gain permissions beyond their authorized scope. Privilege escalation is usually divided into two types: vertical privilege escalation and horizontal privilege escalation. Vertical privilege escalation is when a regular user gains administrator privileges, while horizontal privilege escalation is when a regular user gains access to other regular users' privileges. These vulnerabilities typically exist when user input is not properly validated, access controls are not strict, or there are logical errors in the program.
2. Example 1: Unvalidated User Input
Problematic Code Example:
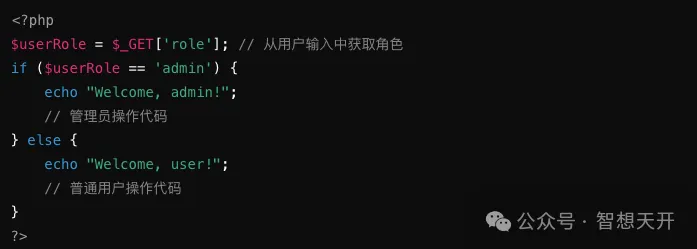
Attackers can modify the role parameter in the URL to escalate privileges. For example, the attacker can use the following url: http://example.com/dashboard.php?role=admin. By modifying the role parameter, the attacker escalates their role to admin, gaining administrator privileges.
3. Example 2: Hardcoded Default Password
Problematic Code Example:
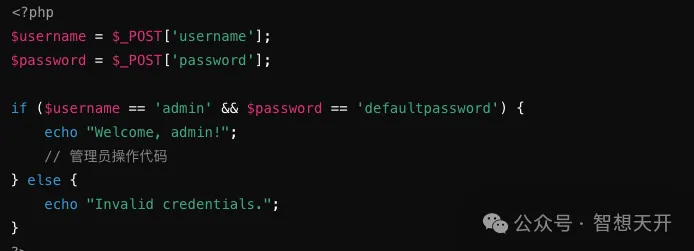
Attackers attempt to log in using the hardcoded default password.
POST /login.php
username=admin&password=defaultpassword
The attacker successfully logs in as an admin by guessing or knowing the default password, gaining administrator privileges.
4. Example 3: Function Lacking Permission Check
Problematic Code Example:
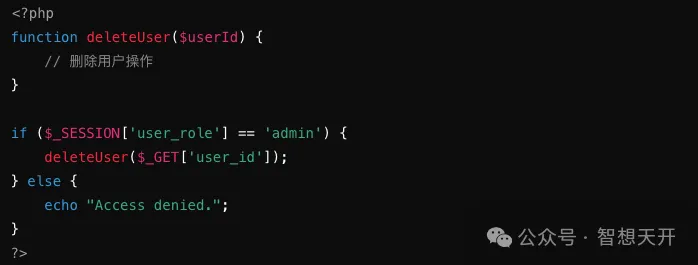
Attackers can delete users by directly calling the function.
5. How to Prevent
5.1. Fix for Example 1: Unvalidated User Input
修复后的安全代码:
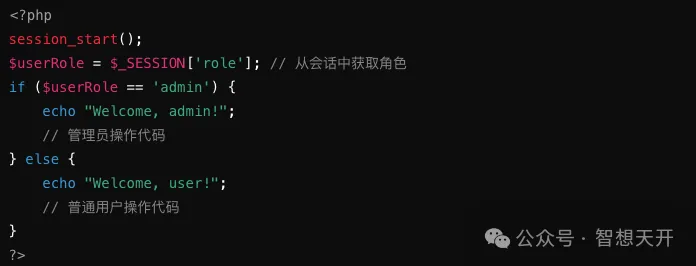
By getting the user role from the session, it ensures the user role is validated, preventing privilege escalation attacks by modifying input parameters.
5.2. Fix for Example 2: Hardcoded Default Password
Fixed Secure Code:
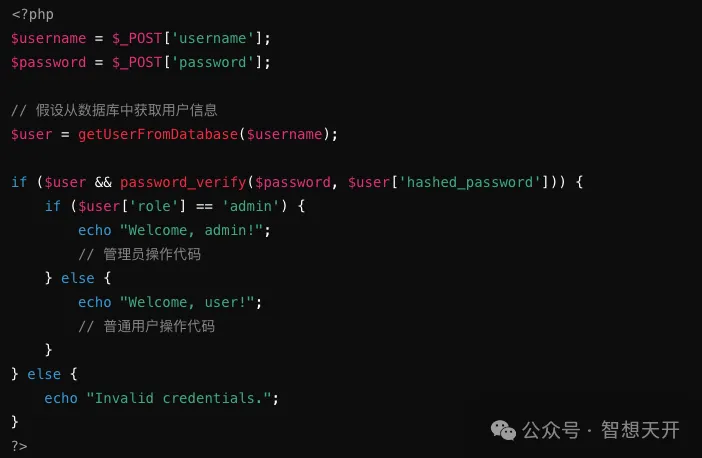
By fetching user information from the database and using a secure password verification method, it prevents the risk of privilege escalation from hardcoded default passwords.
5.3. Fix for Example 3: Function Lacking Permission Check
Fixed Secure Code:
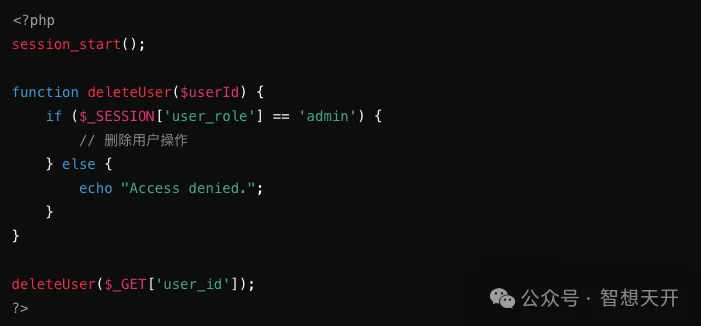
Adding a permission check inside the function ensures that only admins can execute the user deletion operation, preventing privilege escalation attacks by directly calling the function.
6. Additional Knowledge
Access Control Models: Learn about role-based access control (RBAC) and attribute-based access control (ABAC) models to understand how to implement fine-grained permission management.
Secure Coding Practices: Understand and follow best practices for secure coding, such as input validation, output encoding, and the principle of least privilege.
Secure Frameworks and Libraries: Use security-audited frameworks and libraries, such as OWASP's ESAPI, to help implement secure access control.
Deep Learning on Security: Read OWASP guidelines to learn more about privilege escalation and other security issues.

Follow us at WeChat to get more info